We never believe in second chances and Braindump2go brings you the best 70-685 Exam Preparation Materials which will make you pass in the first attempt.We guarantee all questions and answers in our 70-685 Dumps are the latest released, we check all exam dumps questions from time to time according to Microsoft Official Center, in order to guarantee you can read the latest questions!
Vendor: Microsoft
Exam Code: 70-685
Exam Name: Pro: Windows 7, Enterprise Desktop Support Technician
QUESTION 181
Hotspot Question
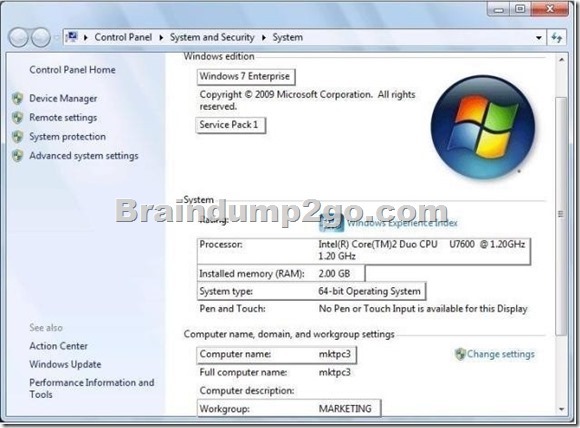
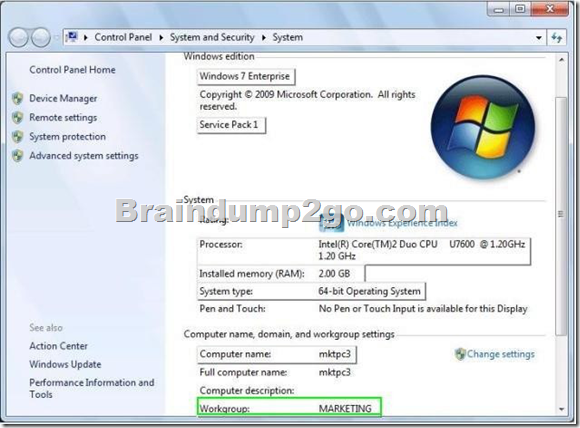
A company has client computers that run Windows 7 Enterprise.
Servers run Windows Server 2008 R2 in an Active Directory Domain Services (AD DS) environment. A server runs the company’s intranet site. Remote access is provided by using DirectAccess.
A user wants to access the intranet site remotely.
You need to ensure that the use’s computer meets the requirements to use DirectAccess.
What should you upgrade or configure?
To answer, select the appropriate area in the work area
Answer:
QUESTION 182
Hotspot Question
A company has computers that run Windows 7 Enterprise.
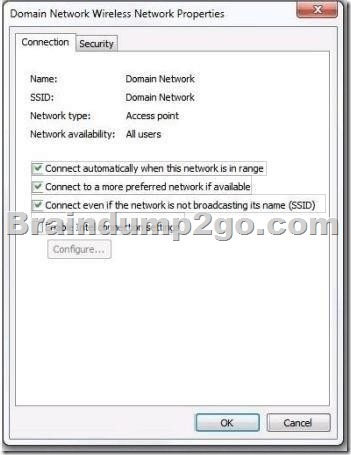
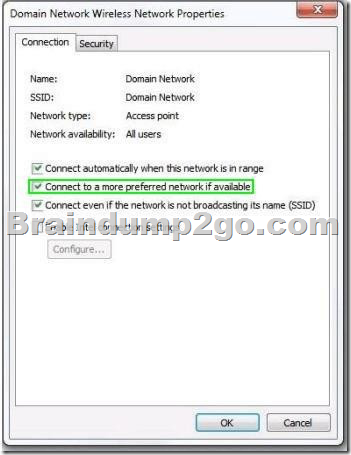
The company has one wireless network named Domain Network, and another wireless network named Internet Network.
Both networks are available in all areas of the building.
A user’s computer automatically connects to Domain Network when it is powered on, but the user wants to connect to Internet Network automatically. Because the user connects to Domain Network occasionally, the network must still be available.
You need to configure the computer to connect to the Internet Network wireless network automatically when the computer powers on.
From the Manage Wireless Networks window, what should you select?
To answer, select the appropriate setting or settings in the work area.
Answer:
QUESTION 183
Hotspot Question
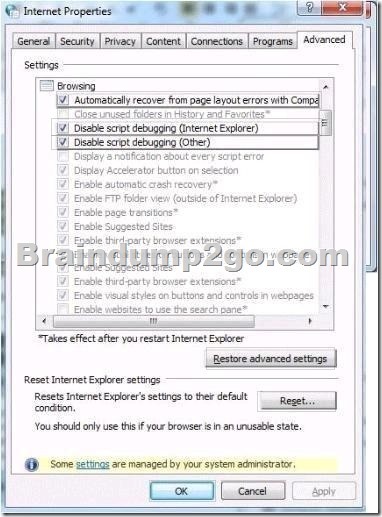
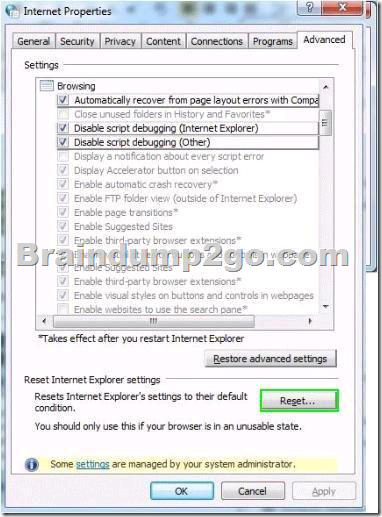
A company has client computers that run Windows 7 Enterprise. A client computer was infected with malicious software that is known to make changes to Microsoft Internet Explorer settings.
The malicious software has been removed from the system by using an antivirus application.
When browsing to sites in Internet Explorer, the user sees a message that says “Internet Explorer cannot display the webpage”.
You need to ensure that the user can browse sites in Internet Explorer without receiving error messages.
Which setting should you select?
To answer, select the appropriate setting in the work area.
Answer:
QUESTION 184
All client computers on your company network were recently upgraded from Windows Vista to windows 7.
Several employees use a scanner to import document images into a database.
They install a new scanning application on their computers.
The application updates the device driver for the scanners as part of the installation process.
Employees report that the application can no longer connect to the scanner.
You need to ensure that the employees can use the scanner.
What should you do?
A. Roll back the device driver to the previous version.
B. Reinstall the application in Windows Vista compatibility mode.
C. Set the application compatibility properties to run the application as an administrator.
D. Restart the computer by using the System Configuration tool to load only basic devices and services.
Answer: A
Explanation:
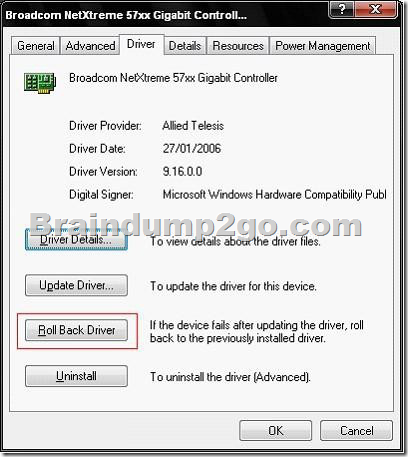
How to Roll Back to the Previous Version of a Device Driver:
Device Driver Roll Back reinstalls the driver you were using previously and restores any driver settings that were changed when you added the new driver.
To roll back a device driver to a previous version:
Log on to the computer by using an account with administrative privileges.
Click Start, and then click Control Panel.
Under Pick a category, click Performance and Maintenance.
Under or pick a Control Panel icon, click System.
On the Hardware tab, click Device Manager.
In the device list, expand the device type branch that you want to work with.
For example, Display adapters.
Right-click the device that you want to work with, and then click Properties.
On the Driver tab, click Roll Back Driver. Click Yes when you receive the following message:
Are you sure you would like to roll back to the previous driver?
The previous device driver is restored. Click Close.
10. Quit Device Manager, and then click OK.
Note: that you cannot restore printer drivers with Device Driver Roll Back. Driver Roll Back only allows you to roll back a driver once. In other words, Windows 7 only keeps a copy of the very last driver installed. It does not keep an archive of all previously installed drivers for the device.
http://pcsupport.about.com/od/windows7/ht/roll-back-driver-windows-7.htm
QUESTION 185
All client computers on your company network run Windows 7. A standard Windows 7 image is loaded on all new computers on the network.
A department in your company purchases several tablet computers.
Employees report that the pen interface does not work on the tablet computers.
You need to ensure that employees can use the pen interface.
What should you do?
A. Turn on the Media Features.
B. Turn on the Tablet PC Components.
C. Start the WMI Performance Adapter service and set it to Automatic.
D. Start the Human Interface Device Access service and set it to Automatic.
Answer: B
Explanation:
Start > Control Panel > Programs > Programs and Features > Turn Windows features on or off
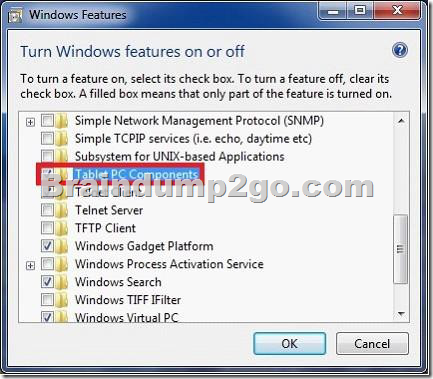
To turn a Windows feature on, select the check box next to the feature. Click OK. To turn a Windows feature off, clear the check box. Click OK.
QUESTION 186
All client computers on your company network run Windows 7.
The preview displayed in the Content view of Windows Explorer and the Search box is considered a security risk by your company.
You need to ensure that documents cannot be previewed in the Content view.
What should you do?
A. Change the Windows Explorer view to the List view and disable all Search indexes.
B. Set Group Policy to enable the Remove See More Results/Search Everywhere link setting.
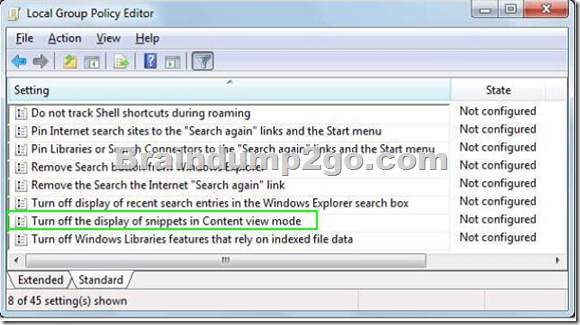
C. Set Group Policy to enable the Turn off the display of snippets in Content view mode setting.
D. Set Group Policy to enable the Turn off display of recent search entries in the Windows Explorer search
box setting.
Answer: C
Explanation:
Location: User Configuration > Administrative Templates > Windows Components > Windows Explorer This policy lets you disable the display of file content snippets when Content view is turned on. Content view is the default view returned when a search is executed and shows snippets of content of returned files.
Default configuration: Snippets are displayed in Content view Purpose:
This policy should be enabled if you want to disable showing snippets of file contents by default when a search is returned. This helps users avoid displaying sensitive data accidentally through Windows Explorer searches while in a non-secure environment. http://technet.microsoft.com/en-us/library/dd744697(WS.10).aspx
http://technet.microsoft.com/en-us/library/dd744697(WS.10).aspx#WS_TurnOffDisplayofSnippets
QUESTION 187
All client computers on your company network were recently migrated from Windows XP to Windows 7.Employees use Internet Explorer 8.
Each time employees access a Web application, they are prompted to install an add-on.
After each installation, the application restarts and prompts the employees to install the add-on again.
You need to ensure that employees can run the application.
What should you do?
A. Use a script to install the add-on in Windows XP Mode.
B. Use a script to run the application in Windows XP Compatibility Mode.
C. Add the class identifier of the add-on to the Add-on list in Group Policy.
D. Set the Deny all add-ons unless specifically allowed in the Add-on list Group Policy setting to Disabled.
Answer: C
QUESTION 188
Your network contains an Active Directory domain. All client computers run Windows 7 Enterprise.
A custom application named App1 is installed on the computers.
All settings for App1 are stored in the user portion of the registry.
The help desk reports a high volume of calls from users who have incorrectly configured the App1 settings.
You need to recommend a solution to minimize the number of help desk calls about the incorrect App1 configurations. Users must be able to use App1.
What should you do?
A. Instruct the help desk to modify the Windows Defender settings.
B. Instruct the help desk to remove all users from the Administrators group on all local computers.
C. Request that a domain administrator create a Group Policy object (GPO) that uses a custom
administrative
template.
D. Request that an administrator create a Group Policy object (GPO) that configures a software
restriction policy.
Answer: C
QUESTION 189
All client computers on your company network run Windows 7 and are members of an Active Directory Domain Services domain.
AppLocker is configured to allow only approved applications to run.
Employees with standard user account permissions are able to run applications that install into the user profile folder.
You need to prevent standard users from running unauthorized applications.
What should you do?
A. Create Executable Rules by selecting the Create Default Rules option.
B. Create Windows Installer Rules by selecting the Create Default Rules option.
C. Create the following Windows Installer Rule:
Deny Everyone – %OSDRIVE%\Users\<user name>\Downloads\*
D. Create the following Executable Rule:
Deny – Everyone – %OSDRIVE%\Users\<user name>\Documents\*
Answer: A
Explanation:
A. Create Executable Rules by selecting the Create Default Rules option. Many organizations are implementing standard user policies, which allow users to log on to their computers only as a standard user. With Windows Vista®, this task became easier. However, more independent software vendors (ISVs) are creating per-user applications that do not require administrative rights to be installed and that are installed and run in the user profile folder. As a result, standard users can install many applications and circumvent the application lockdown policy. With AppLocker, you can prevent users from installing and running per-user applications.
To prevent standard users from running per-user:
To open the Local Security Policy MMC snap-in, click Start, type secpol.msc in the Search programs and files box, and then press ENTER.
In the console tree, double-click Application Control Policies, and then double-click AppLocker. Right-click Executable Rules, and then click Create Default Rules. http://technet.microsoft.com/en-us/library/dd723685(WS.10).aspx
QUESTION 190
All client computers on your company network run Windows 7 and are members of an Active Directory Domain Services (AD DS) domain.
The help desk reports that several computers that run Windows 7 Enterprise have bad sectors on their hard disks.
You need to minimize the loss of data on the computers caused by storing data on the bad sectors.
Which command should you run?
A. chkdsk.exe /r
B. chkdsk.exe /f
C. defrag.exe /c
D. defrag.exe /x
Answer: A
QUESTION 191
All client computers on your company network run Windows 7 and are members of an Active Directory Domain Services (AD DS) domain.
The help desk reports that several computers that run Windows 7 Enterprise have bad sectors on their hard disks.
You need to minimize the loss of data on the computers caused by storing data on the bad sectors.
Which command should you run?
A. Run chkdsk.exe /r.
B. Run defrag.exe c: /a.
C. Modify the System Protection settings.
D. Modify the Write Caching Policy for the disk.
Answer: A
Explanation:
chkdsk.exe
Check Disk – check and repair disk problems
Syntax: CHKDSK [drive:] [[path] filename] [/F] [/V] [/R] [/L [: size]] Key
[drive:] The drive to check.
Filename File(s) to check for fragmentation (FAT only). /F Automatically Fix file system errors on the disk. /X Fix file system errors on the disk, (Win2003 and above) dismounts the volume first, closing all open file handles.
/R Scan for and attempt Recovery of bad sectors.
/V Display the full path and name of every file on the disk.
/L: size NTFS only: change the log file size to the specified number of kilobytes. If size is not specified, displays the current log size and the drive type (FAT or NTFS).
/C Skip directory corruption checks.
/I Skip corruption checks that compare directory entries to the file record segment (FRS) in the volume’s master file table (MFT)
QUESTION 192
Hotspot Question
All client computers on a company’s network run Windows 7.
The preview displayed in the Content view of Windows Explorer and the Searchbox is considered a security risk by the company.
You need to ensure that documents cannot be previewed in the Content view.
Which setting should you select in the Local Group Policy Editor?
To answer, select the appropriate group policy in the work area.
Answer:
QUESTION 193
Drag and Drop Question
A company has computers in a London office running Windows 7 Enterprise, and a server located in a New York office running Windows Server 2008 R2. The New York server is configured for Active Directory Domain Services (AD DS) and as a file server. Users connect to the file server by using a Virtual Private Network (VPN), which requires two-factor authentication.
Some users in the London office frequently are locked of out their VPN accounts.
You need to recommend a solution to reduce support incidents regarding VPN logon issues while still providing remote access.
Which technology should you recommend?
(To answer, drag the appropriate item from the list of items to the target in the work area.)
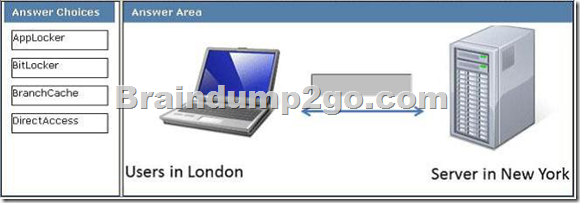
Answer:

QUESTION 194
Hotspot Question
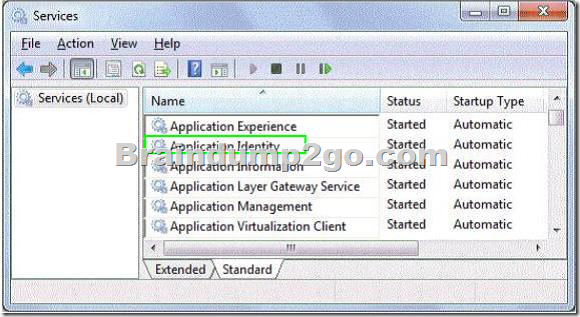
A company has computers running Windows 7 Enterprise.
The company enforces AppLocker policies to prevent unwanted applications from running.
A user wants to evaluate an application, but is blocked by AppLocker policies.
You need to stop AppLocker policies from being enforced on the user’s computer.
Which service should you disable to accomplish this goal?
To answer, select the appropriate service in the work area.
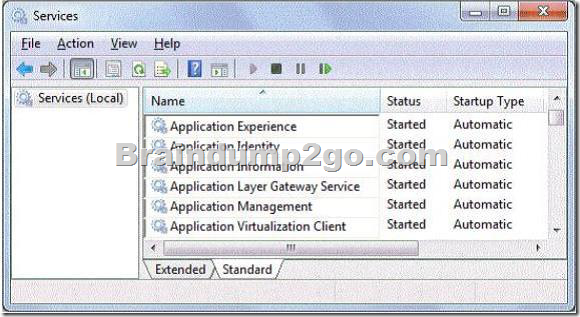
Answer:
QUESTION 195
Hotspot Question
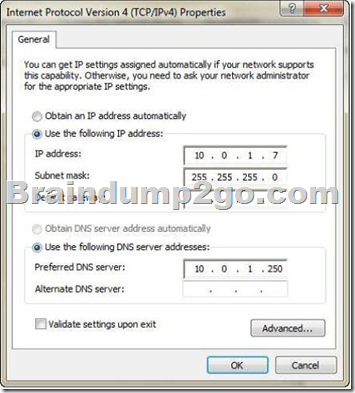
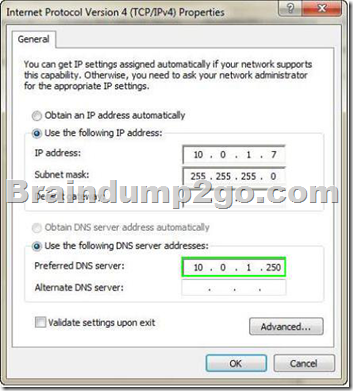
A company has client computers that run Windows 7 Enterprise, a single subnet, and servers that run Windows Server 2008 R2.
A client computer can connect to the company’s servers by using IP addresses, but not by using fully qualified domain names (FQDNs).
You need to ensure that the client computer can resolve to the company* s servers by using FQDNs.
Which addresses should you change?
To answer, select the appropriate addresses in the work area.
Answer:
QUESTION 196
Hotspot Question
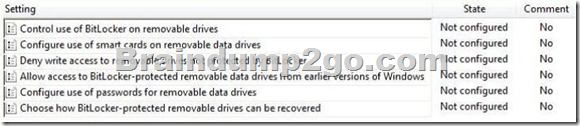
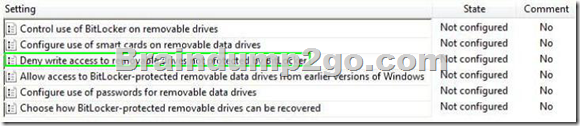
All client computers on your company network run Windows 7.
The computers are members of a Windows Server 2008 R2 domain.
You need to use Group Policy to ensure that data stored on removable drives is encrypted.
Which setting should you select?
To answer, select the appropriate setting or settings in the work area.
Answer:
Instant Download Braindump2go New Released Microsoft 70-685 Exam Dumps PDF & VCE! Enjoy 1 year Free Updation! 100% Exam Pass Guaranteed Or Full Money Back!